BLOG 22 December 2021
Ollie, your personal Microsoft Sentinel assistant
At The Collective, we are constantly looking to innovate and push the boundaries of the existing (Microsoft) capabilities. For the 2021 Microsoft Sentinel Hackathon, we developed an assistant for Microsoft Sentinel which will ease the day-to-day management of the SIEM & SOAR tool.
The solution, aptly named Ollie after it’s developer, is based on the Teams Bot Framework and uses the Microsoft Sentinel API & Microsoft Security Graph to interact with Microsoft Sentinel. Ollie offers extremely easy and low effort interaction with your Microsoft Sentinel environment, which decreases the need to open the Microsoft Sentinel portal in order to execute small tasks.
At The Collective, we strongly believe in community interaction and feedback and are open-sourcing the entire solution. All files (including installation files and source code) are publicly available.
Introducing Ollie
Ollie is meant to provide an easy to use interface for Microsoft Sentinel to decrease the workloads for security administrators. There are a couple of different reasons for this:
- Within multiple organizations, we have observed that security administrators are often tasked with constantly updating information with the SIEM (ranging from a list of high privileged users to adding Threat Intelligence indicators). Administrators are often extremely busy and lack behind on tasks like this, which could put an organization at risk. By delegating these tasks to other people, more time is created for administrators.
- Analysts will need to open up the Microsoft Sentinel portal multiple times a day to update the information. Authenticating and navigating to the correct part of the portal can be extremely time consuming (as the portal is sometimes excruciating slow unfortunately…).
In order to overcome these issues, Ollie was born. Ollie consists out of two main parts:
- The backend infrastructure which runs the ‘brain of the bot’ which hosted on Azure PaaS components.
- The Teams application which contains the user interface that needs to be deployed to Teams.
Ollie in action
Ollie’s capabilities are currently focused on two main capabilities which are watchlists and Threat Intelligence. The integration between our assistant and watchlist is extremely easy and always you to update existing watchlist from within your Teams clients. Watchlists are often updated often to feed Microsoft Sentinel with supporting data (such as information about the public IP addressed used or a list of high value devices). By using Ollie, you are able to easily add or remove items from a watchlist, which ensure this information is kept up to date without much effort.

Besides watchlists, Ollie also manages Threat Intelligence (TI) Indicators. TI indicators can be added to provide additional information about current attacks in order to identify potential attacks which might have been unnoticed by your existing security systems. Besides the ability to easily add new Threat Intelligence Indicators, Ollie will also search your logs in order to verify if the indicator has been spotted within your environment for the last 90 days. If a hit was found, an Microsoft Sentinel incident will be automatically created for the SOC to investigate.
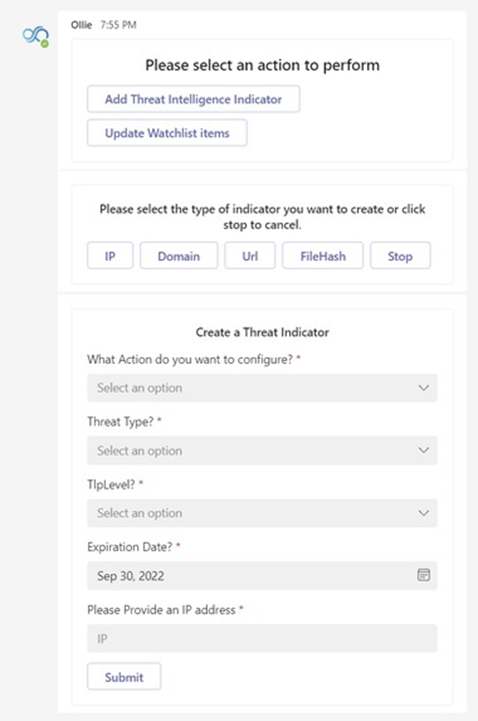
Behind the scenes
Ollie is natively built on top of Azure PaaS solutions for it’s hosting and interacts with Microsoft Sentinel through API’s. Ollie consists of the following Azure components:
- Azure App Service
- Bot Channels Registration
- Azure Key Vault
In order to interact with Microsoft Sentinel watchlists and add Threat Intelligence indicators (which is done through the Microsoft Security Graph API) an app registration needs to be created with permissions to update Microsoft Sentinel watchlists and add new TI indicators.
As anybody with access to the bot can create new Threat Intelligence Indicators, you need to ensure the Teams application is properly secured and cannot be used by unauthorized users. Within the Teams Admin Center, the application needs to be uploaded as a custom application.
Depending on your Teams configuration, this application could be available to every user within your tenant. It is recommended to scope the application to a subset of users by using a permission policy. Such a policy will ensure only authorized users can access Ollie to interact with Microsoft Sentinel.
What makes Ollie unique, is the way it searches for hits of TI indicators. Normally, scheduled analytic rules are available which will compare all TI indicators with your logs, if any hits are found an incident will be created. Unfortunately, analytic rules can only have a lookup period of 14 days, which means it can only retrieve data from the past 14 days. This means an incident will not be created when an indicator appeared longer than 14 days ago. In order to solve this issue, Ollie uses to Log Analytics API to query for any hits within the last 90 days. To support a wide range of data sources (including custom data), the searches are run by using normalization schemas.
Normalization schemas are Microsoft Sentinel’s way of using one query to search multiple tables at once. By using these schemas, it’s easy to search a wide range of sources without needing to update queries for every source. If you want to use a custom data sources, just expand the parser and Ollie will include it in its next searches!
Looking forward to feedback!
During our efforts within the Microsoft Sentinel hackathon, we created an initial MVP for the Microsoft Sentinel assistant. We still have lots of ideas to expand it’s capabilities, this includes the ability to manage analytic rules, orchestrate incidents by interacting with Playbooks and execute hunting queries from your Teams client. If you have any feedback or insights, feel free to leave a comment or contact me through social media.
At The Collective, we constantly push the boundaries of technology. Looking for a partner that helps your organizations to achieve more through secure and innovative technologies, solutions and services?
Johan Delimon
COO
Focus
- Teams Voice
- Teams Meeting Rooms
Bio
- Microsoft Teams & Skype for Business MVP, MCSM, Microsoft Trainer, Enterprise Architect & Community Leader
The Collective is a highly-skilled Microsoft partner with expertise in security, compliance, endpoint management, messaging, and Microsoft Teams voice and meetings.
© The Collective - BE 0726.449.826 - Privacy Policy